| Previous Next Index Image Index Year Selection | |
|
|
1. Overview of high-technology offenses High-technology offenses are those offenses that are committed by misusing computer and telecommunication technology.They are roughly categorized into following three groups:(a) computer offenses in narrow sense;(b) network offenses ;and(c) unauthorized computer accessing acts,etc.
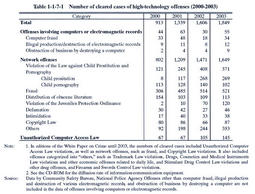
Computer offenses in the narrow sense refer to offenses targeting computers or electromagnetic records,and include computer fraud,obstruction of business by destroying a computer,etc.,and illegal production,use,and destruction of various electromagnetic records. Network offenses refer to offenses committed by using computer networks,and include various types of offenses such as fraud,sales of illegal goods,and the sales/distribution of child pornography committed by using the Internet. Unauthorized computer accessing acts,etc.are the offenses provided in the Unauthorized Computer Access Law that entered into force in February2000.Under the Law,such unauthorized computer accessing acts shall be punished as acts of providing the other parties with ID numbers or passwords of other persons,as well as acts of using ID numbers or passwords of other persons via the Network without permission and giving illegal information or commands to the other party's computer system while taking advantage of defects in the system,thereby making specific limited-access computers accessible. (1) Clearanceof of fenses Table 1-1-7-1 shows the number of cleared cases for high-technology offenses over the last four years,by type of offense.Among computer offenses in narrow sense,the number of cleared cases involving computers or electromagnetic records(only those listed in the Table )is relatively small and has remained flat.
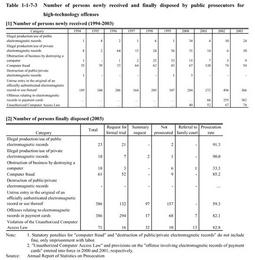
On the other hand,cases for network offenses have grown,among which fraud is the most common every year,accounting for about30%of the total,followed by violations of the Law against Child Prostitution and Pornography since2001.Others"include various offenses such as stimulant drug and other drug offenses,and violations of the Trademark Law(Law No.127of1959),Drugs,Cosmetics and Medical Instruments Law(Law No.145of1960),and Firearms and Swords Control Law. Cleared cases of Unauthorized Computer Access Law violations have been relatively small but increased slightly since the Law was enforced in2000. Table 1-1-7-2 shows the number of handguns seized and recognized by the police to have been traded via the Internet over the last five years.In2003,such handguns account for25.6%of the total,which indicates that computer networks are misused for offenses that would affect public security. Table 1-1-7-1 Number of cleared cases of high-technology offenses(2000-2003) Table 1-1-7-2 Number of seized handguns traded via the Internet(1999-2003) (2) Disposition by public prosecutors and bycourts Table 1-1-7-3[1] shows the numbers of persons newly received by public prosecutors offices over the last10years for high-technology offenses,by type of offense. Table 1-1-7-3[2] shows the number of persons finally disposed by public prosecutors in2003for these offenses.Among those offenses for which the number of persons disposed was large,prosecution rate was slightly less than60%for untrue entry in the original of an officially authenticated electromagnetic record or use thereof,and stayed within the80-90%range for offenses involving electromagnetic records in payment cards,computer fraud,and Unauthorized Computer Access Law violations.All these rates are higher than the prosecution rate of overall non-traffic penal code offenses(53.3%)in2003.
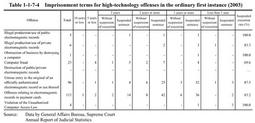
Table 1-1-7-3 Number of persons newly received and finally disposed by public prosecutors for high-technology offenses Table 1-1-7-4 shows the term of imprisonment with labor sentenced in the ordinary first instance for high-technology offenses in2003.Table 1-1-7-4 Imprisonment terms for high-technology offenses in the ordinary first instance(2003) |